Introduction
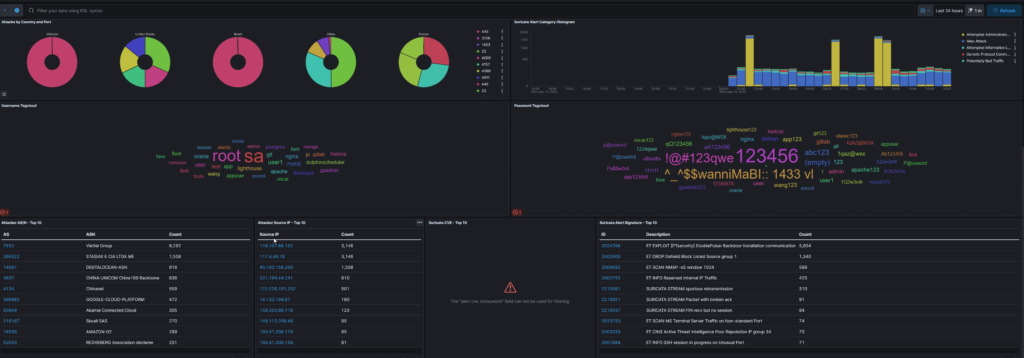
Monitoring and analyzing potential threats is crucial for understanding cybersecurity. To achieve this, I deployed T-Pot a multi-honeypot framework that combines several honeypot technologies into a single system. With T-Pot running in a AWS Instance, I can capture, log, and analyze malicious activity , gaining valuable insights into real-world attack patterns.
Story
I first started by going to AWS (Amazon web services) , from there it allowed to launch an instance where i could install T-POT .
After much set up for the installation this was my first boot up so there wasn’t much data.
I left this running for about 3 days and i had over 13k hits to the honeypot. Most of them where from Dionaea which logs attempts to exploit protocols like SMB, HTTP, and FTP and Cowrie which simulates a SSH and Telnet server.